Introduction
As an IT admin or manager, you are responsible for ensuring that your organization’s devices and data are secure and compliant with the relevant policies and regulations. You also want to provide your users with the best experience and productivity tools, without compromising on security. How can you achieve this balance?
One of the solutions is to use Microsoft Intune, a cloud-based service that allows you to manage and secure your devices and data from a single console. Intune lets you create and enforce policies and compliance rules for your devices, apps, and data, regardless of where they are located or what platform they run on. You can also monitor and report on the status of your devices and data and take remedial actions if needed.
In this blog post, we will show you how to use Intune to secure your devices and data with policies and compliance. We will cover the following topics:
- What are policies and compliance in Intune?
- How to create and assign policies and compliance rules for your devices and data
- How to monitor and report on the compliance status of your devices and data
- How to take actions on non-compliant devices and data
What are policies and compliance in Intune?
Policies and compliance are the core features of Intune that allow you to define and enforce the security and configuration settings for your devices and data. Policies and compliance can help you to:
- Protect your devices and data from unauthorized access, malware, and data loss.
- Ensure that your devices and data meet the standards and regulations of your industry and region.
- Control the features and functions of your devices and apps.
- Optimize the performance and battery life of your devices.
- Customize the user experience and preferences of your devices and apps.
There are two types of policies and compliance in Intune: device policies and app protection policies. Device policies apply to the whole device and its settings, while app protection policies apply to specific apps and their data. You can create and assign different policies and compliance rules for different groups of devices and users, depending on your needs and scenarios.
How to create and assign policies and compliance rules for your devices and data
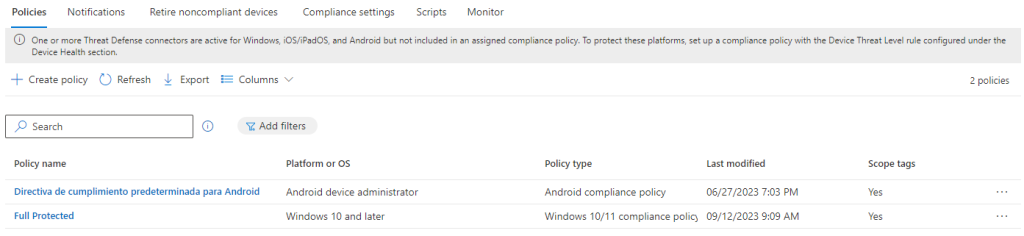
To create and assign policies and compliance rules for your devices and data, you need to follow these steps:
- Sign in to the Microsoft Endpoint Manager admin centre with your Intune credentials.
- Go to the Devices or Apps section, depending on whether you want to create device policies or app protection policies.
- Select the type of policy or compliance rule you want to create, such as configuration profiles, compliance policies, app configuration policies, or app protection policies.
- Click on Create policy or Create profile and follow the wizard to configure the settings and rules for your policy or profile.
- Click on Next and assign the policy or profile to the groups of devices or users you want to apply it to
- Click on Create to finish the process and deploy the policy or profile to your devices or users.
You can also edit, delete, or duplicate your policies and profiles at any time, or create custom policies and profiles using PowerShell or Graph API.
How to monitor and report on the compliance status of your devices and data
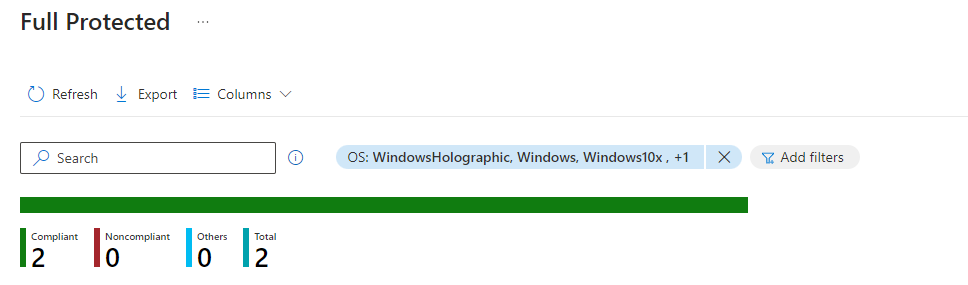
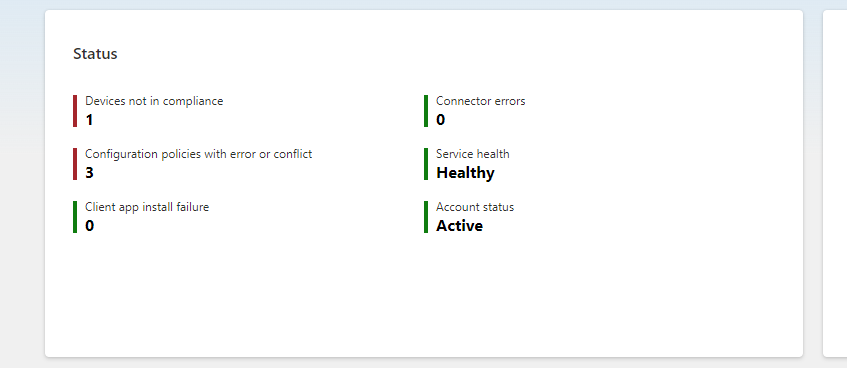
After you create and assign your policies and compliance rules, you can monitor and report on the compliance status of your devices and data using the Intune dashboard and reports. The dashboard and reports can help you to:
- View the overall compliance status of your devices and data and identify any issues or gaps.
- Drill down into the details of each device, user, app, or policy, and see the compliance status, settings, and actions.
- Filter, sort, and export the data for further analysis and reporting.
- Generate and schedule custom reports using PowerShell or Graph API
To access the dashboard and reports, you need to go to the Microsoft Endpoint Manager admin centre, and then go to the Devices or Apps section, depending on whether you want to monitor device policies or app protection policies. You can then select the type of policy or compliance rule you want to monitor, such as configuration profiles, compliance policies, app configuration policies, or app protection policies. You can then click on the Overview or Reports tabs to see the dashboard and reports for your selected policy or compliance rule.
How to take actions on non-compliant devices and data
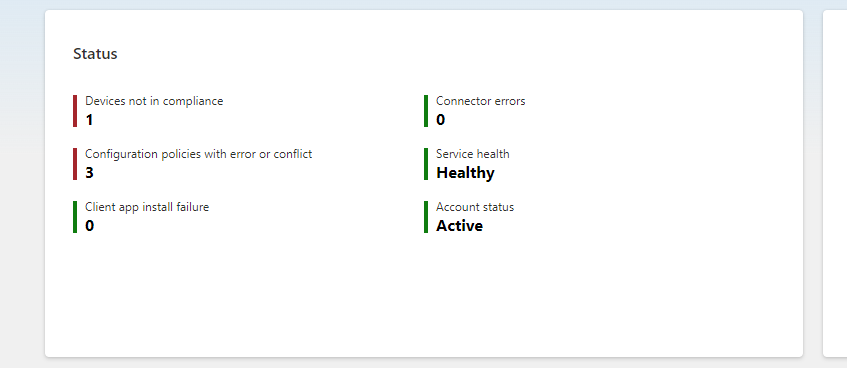
If you find any non-compliant devices or data, you can take actions to remediate them and bring them back to compliance. You can take actions on non-compliant devices or data using the Intune console or PowerShell. The actions you can take include:
- Notify the user or the admin of the non-compliance issue and the steps to resolve it.
- Block or allow access to corporate resources, such as email, SharePoint, or OneDrive
- Wipe or retire the device or app and remove the corporate data.
- Reset the device or app to the factory settings.
- Lock or unlock the device or app.
- Update or reinstall the device or app.
- Change the device or app settings or configuration.
To take actions on non-compliant devices or data, you need to go to the Microsoft Endpoint Manager admin centre, and then go to the Devices or Apps section, depending on whether you want to take actions on device policies or app protection policies. You can then select the type of policy or compliance rule you want to take actions on, such as configuration profiles, compliance policies, app configuration policies, or app protection policies. You can then click on the Devices, Users, or Apps tabs to see the list of devices, users, or apps that are affected by your selected policy or compliance rule. You can then select the device, user, or app you want to act on, and click on the Actions button to see the available actions for your selected device, user, or app. You can then choose the action you want to take and confirm it.
Conclusion
In this blog post, we have shown you how to use Intune to secure your devices and data with policies and compliance. We have explained what policies and compliance are, how to create and assign them, how to monitor and report on them, and how to take actions on them. We hope that this guide will help you to use Intune to protect your organization’s devices and data and provide your users with the best experience and productivity tools.
If you want to learn more about Intune and its features, you can visit the following resources:
2 Replies to “How to Secure Your Devices and Data”
Comments are closed.